Understandable analogies and Confidential Computing
I thought I’d take a break from my recent musing about LLMs hence this post which arose after reading a colleague’s analogy to explain some confidential computing concepts that inspired me to write a version of my own but with a different analogy ( Thanks to him indoors for the inspiration for that. !)
If you’ve read any of my posts before you are aware that I enjoy trying to demystify things. One way I do this is by using real-world analogies or at least analogies that are understood when I can’t really see a way to shoehorn in a flow chart. Technical concepts can be difficult to understand for the lay(wo)man or even folks in tech not having a background in a particular part of tech , especially for those who are not familiar with the jargon! As you know, tech is just full of jargon .
I have had a lot of success over the years in getting concepts across by using analogies that are understood outside of my tech bubble. One of my more recent examples was when I discussed defence in depth by talking about castles here . I’m sure it wasn’t just the mention of murder holes why folks seemed to enjoy reading it!
I’ve been using this method for years. I think the earliest one I used was to explain TCP/IP routing by using the analogy of sending a snail mail letter. It’s a common analogy used now but back then not so much.
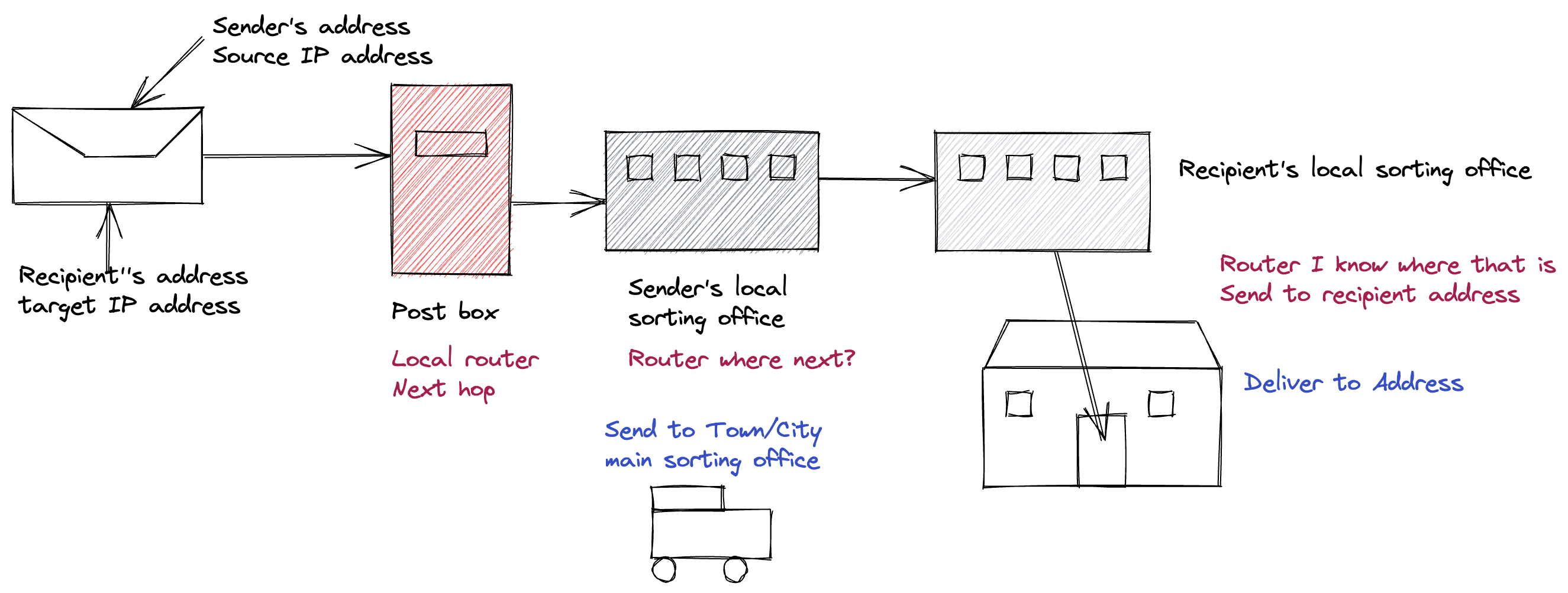
You put both your address and your recipients address on the envelope then put it in a post box From there it is taken to the local sorting office where they figure out where to send the letter to next . They do this by looking at the Town and post code . If its local then the local postie will deliver but as in our scenario its in another town ( network) it has some travelling to do .
I’d explain how routers look up next hop using their local routing tables and how this is like a sorting office looking at the address and saying okay I need to send this to that town next .
I’d explain how the parts of the address are used to route the letter and get closer to the actual house number on a specific street in a specific town.
I would explain how you can think of the host address as being the house /apartment number and the network being the area ( district I guess ) with the subnet being the street . The postcode represents this later part and is the key identifier that allows a snail mail letter to get from the recipient to the recipient.
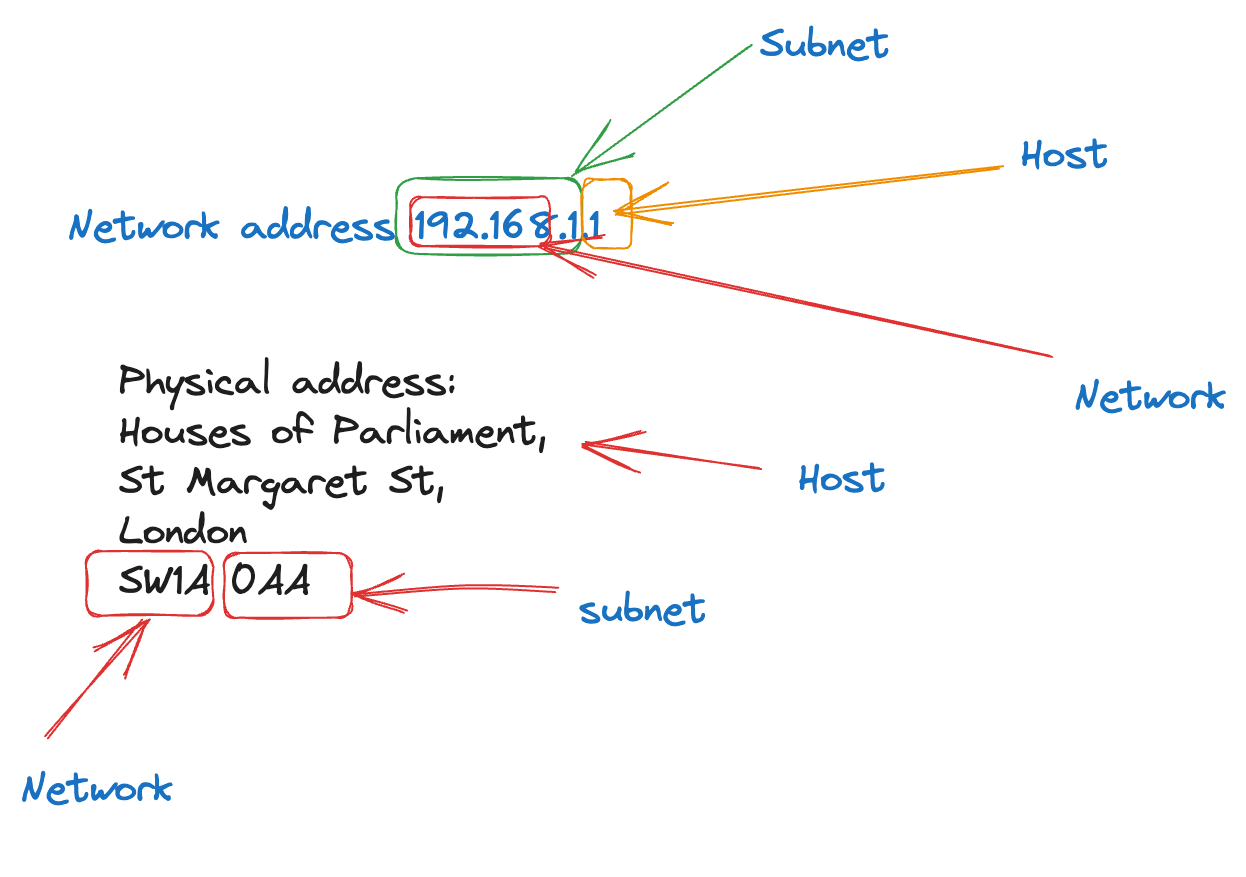
IPv4 is just easier to use in this example.
I’d explain how a postcode has a number of houses/ apartments that share the same postcode and this is like the subnetwork the IP address belongs to.
And I’d inevitably start talking about DNS but after listening to me talk about posting letters and postcodes I would watch their eyes glaze over 😂
It’s a lot more words than that but you get the drift I hope!
Another one I’m fond of using is car tyres to explain the cold, warm and hot DR patterns as shown in the GCP DR planning guide I worked on .
I used this photo. All cars gave permission. I didn’t & still don’t drive a humongous US truck type car or a Beemer!

I then explained in terms of cold, warm & hot patterns what state of preparedness you are for a flat tire.
So just cutting & pasting from the guide :
Cold: You have no spare tire, so you must call someone to come to you with a new tire and replace it. Your trip stops until help arrives to make the repair.
Warm: You have a spare tire and a replacement kit, so you can get back on the road using what you have in your car. However, you must stop your journey to repair the problem.
Hot: You have run-flat tires. You might need to slow down a little, but there is no immediate impact on your journey. Your tires run well enough that you can continue (although you must eventually address the issue).
I also asked ChatGPT & bard for real world examples for the DR scenario but I guess they don’t actually have experience of the real world . One wasn’t even explaining DR & the other one wasn’t real world. Guess my job is safe for a while yet!
Confidential computing is gaining traction as it provides encryption in use to party down with encryption in transit & at rest.
Google cloud has a number of flavours of confidential computing options but we are just going to focus on Confidential VMs and Confidential Space using a bank and safety deposit boxes for the analogy.
First let’s set up the scene
-
We have a bank ( Think of this as being Google Cloud)
-
We have the bank tellers
-
We have the bank assistant(s)
-
We have you
-
We have a collaborator
Imagine a bustling bank. The booths or protected counters where the bank tellers work are like standard virtual machines (VMs). There is no encryption in use when using standard VMs so unless you put in place the appropriate controls for the use of the standard VM its contents can be viewed by anyone with the inclination to have a look ( Don’t do this use best practices and secure access to your VMs ). Anyone if they pass by or are standing in line behind you are able to see your transaction, for example collecting some documents from the bank vault to be handed over to you .
Humour me here as sure you can put controls in place like using firewalls rules and preventing unauthorized access to your VMs but in the case of the bank scenario the teller is permitted to see your documents that were fetched from the vault . Anyone with the inclination can come stare at your interaction with the teller!
You decide you’d like a little more privacy with regards your activities at the bank and you have paid for a safety deposit box. This allows you to collect your documents in private with no one observing what you are doing.
The safety deposit box is held in a secure room. You have the only key to your safety deposit box. A bank assistant opens the door to the room and leaves you alone to locate, open and put something into your safety deposit box or take something out. On completion of your activities you relock the deposit box and put it back where it belongs. You knock on the door to let the bank assistant know you have finished and you want to leave the room now.
This is similar to using a confidential compute VM where it ensures that your data and applications stay private and encrypted even while in use ( the activities within the room ) . It does this by encrypting the VM memory with a dedicated per-VM instance key that is generated and managed by the processor. These keys are generated by the processor during VM creation and reside solely within it, making them unavailable to Google or other VMs running on the host. Once the VM is terminated the key is no longer usable as it only resides within the VM.
Now imagine you are a spy master and you need to exchange stuff with a contracted agent . You have a safety deposit box that has a bunch of passports for different countries in it. The agent has a deposit box at the same bank with reports for the various agencies they have been contracted to work for . The agent needs a passport in a hurry and you want their report. You both have keys for a third safety deposit box. Only one person can be in the room at a time .
The following process occurs
- You enter the room, retrieve and open the safety deposit box ( box 1) only you have access to .
- You remove a passport for say dodgy location 1 . You lock this safety deposit box and replace it on its shelf .
- You then get safety deposit box 2 open it and place the passport in that box. You lock this box and place it back on its shelf
- You leave the room
- Later that day the agent enters the room retrieves box 3 which they only have access to. They remove the report you need , then they lock the box and replace it on its shelf .
- They then get box 2 which you both have keys to. They open it retrieve the passport you left earlier then place the report in the box .
- They lock box 2 replace it and then leave the room
- Later that day you get message that the agent has left the report and retrieved their passport
- You go back to the bank the following morning to retrieve the report from the shared safety deposit box 2
This is very much like using Confidential Space. Confidential Space allows you to perform tasks such as joint data analysis and machine learning (ML) model training with trust guarantees that the data being contributed by partners in the collaboration are confident their data can stay protected from their partners including hardened protection against the cloud service provider access. Let’s break this down
Confidential space is built on top of Confidential VM so think of this of this as the safety deposit box room
The scenario described is an example of a multi party computation . Both datasets remain confidential to the owner of the dataset but the workload can access the datasets to produce a result that is shared .
Breaking this down to the moving parts required
- Confidential data - Passports in box 1 and the Reports in box 2
- Encryption keys to encrypt the data and keep it confidential. The keys to the safety deposit boxes and the key to get into the room
- A place to store the encrypted data in. This is very often Cloud storage. In our scenario this is the safety deposit boxes .
- A trusted workload The exchange process
- An attestation process This detects modifications to the workload image or its TEE. This control helps protect the workload’s integrity pre-attestation.
- you would need a service account that has access to the encryption keys, so it can decrypt the confidential data. ( I’m not going to try and create a convoluted mapping for this; I’ll leave this as an exercise for the reader to figure out!)
- A workload identity pool with that service account connected to it. The workload processing the confidential data uses the pool to impersonate the service account and retrieve the unencrypted data.
- Both you, the spymaster and the agent, need to be authorized to do your respective parts. You both have a key to the shared deposit box and you both have exclusive access to your source data via the individually accessible deposit boxes which contain the pile of passports and pile of reports respectively.
- You can think of you and the agent as being resource owners. A resource owner can access their own data, set permissions on that data, and access the workload’s results based on that data. They can’t access the other resource owner’s data, or modify the workload code by themselves. You have sole access to your passports and the agent has sole access to the report they have created .
- The department that wrote the process to be followed for exchanging of documents can be considered the Workload author
- The bank assistant can be considered the workload operator as without them letting you into the room the process can not occur. The operator doesn’t have access to the data or the results, and can’t influence or modify the code or execution environment. In addition, the operator doesn’t control access to the data or the results.
- The completion of the process is when you have retrieved the final report.
The following diagram shows how the scenario described maps to the system components and parties
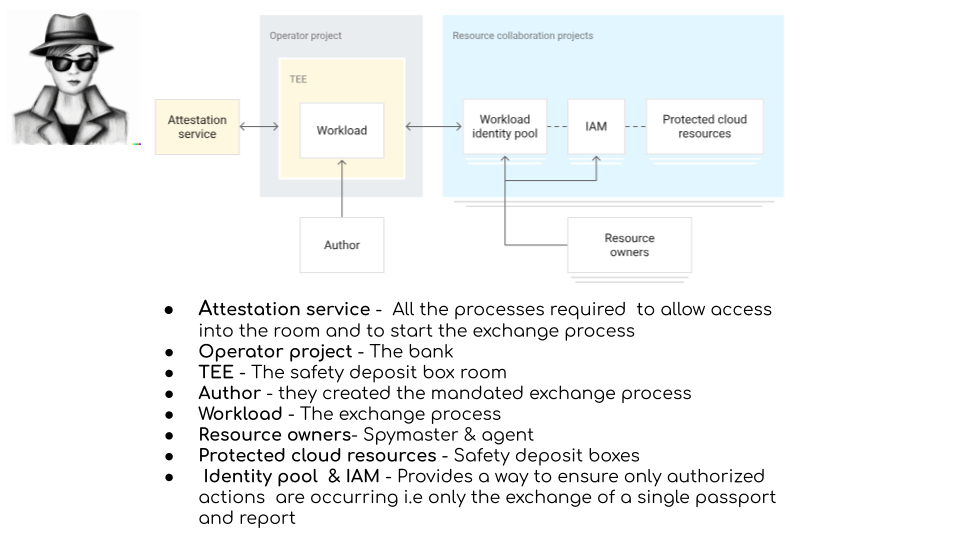
Thanks to DALL.E-2 for interpreting my prompt appropriately for a spy wearing a hat & dark glasses
What role is being played by whom can be mixed and matched the key thing is ensuring any role only has the access they need .
And a shout out for my fav codelab for showing how to use Confidential Space while I’m here !